Beautiful Tips About How To Get Rid Of Buffer Overflow

If the first step to detect buffer overflows in the source code is understanding how they work, and the second step is knowing to look for external input and buffer.
How to get rid of buffer overflow. What are buffer overflow attacks? It’s time to get into buffer overflow exploitation using stack. Vectors, for example, have out of bounds detection if you use at intead of [] for indexing.
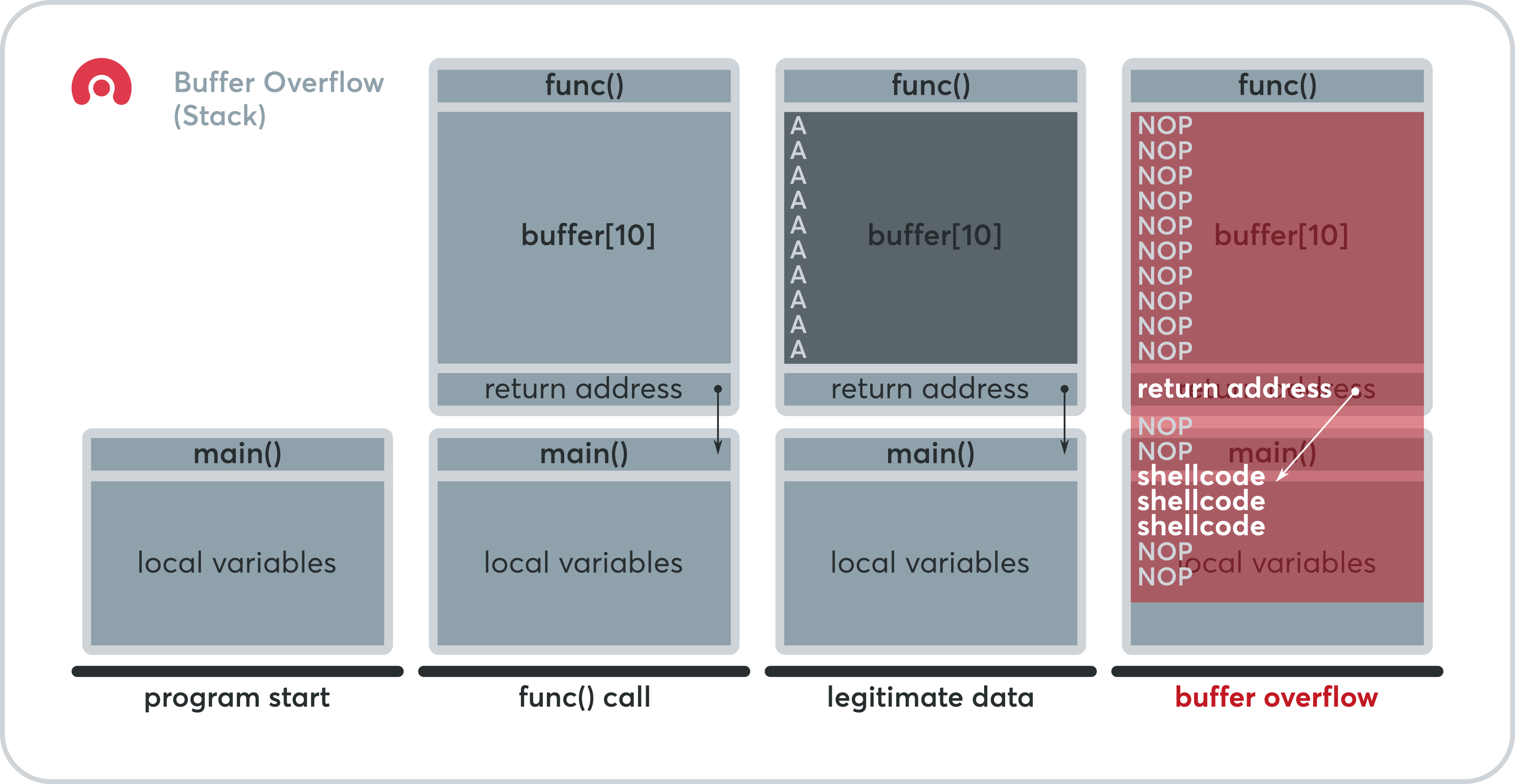
Before that, let’s try to understand how a stack is built for any function. The extra data can overflow into adjacent memory. Exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables.
Exploiting buffer overflow. We're here to help. Besides, since there are three buffers, can i construct three bufs, the first two bufs include nop slide.
If the first step to detect buffer overflows in source code is understanding how they work, and the second step is knowing to look for external input and buffer. In a c program, you can allocate memory on the stack, at compile time, or on the heap, at run time. A buffer overflow attack can be:
September 27, 2023 the term “buffer” is a generic term that refers to a place to store or hold something temporarily before using it, in order to mitigate differences. In order to understand buffer overflows, it's important to understand a little about how programs allocate memory. To successfully mitigate buffer overflow attacks, it is important to understand how they unfold.
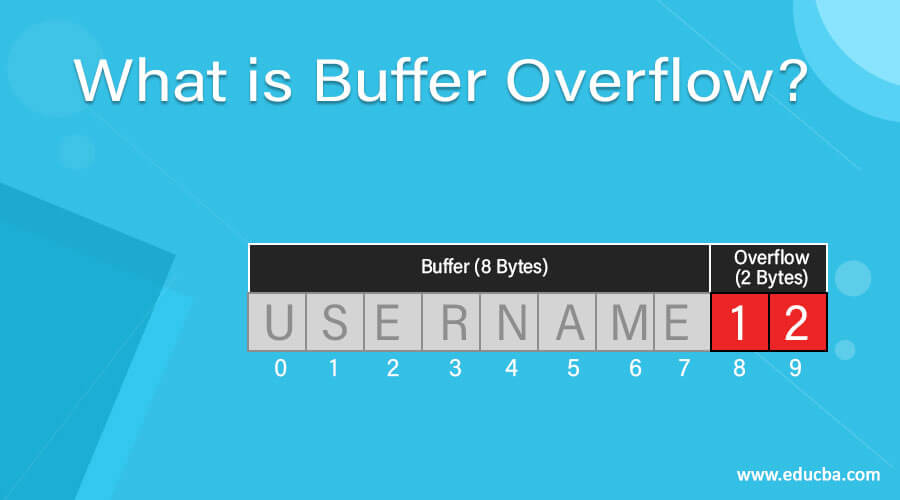
Simply put, buffer overflow refers to a program writing content to memory outside of the buffer (as a result of overflow). Is there any way to resolve this error from client side like fetching the data in form of batches or it should be done something from the apigee or server side. Buffer overflow attacks generally occur when you try to write to a memory location you do not own.
Fortunately, it is possible to avoid scanf buffer overflow by either specifying a field width or using the a flag. Buffers are designed to contain specific amounts of data. Read on to learn how they work and then identify best.
The following are some of the common buffer overflow types. What are buffer overflows buffer overflows were one of the first methods of exploiting systems known to hackers and penetration testers. The buffer overflow vulnerability occurs whenever data written to a buffer exceeds its size.
Simply put they provide a. A buffer overflow is a type of runtime error that allows a program to write past the end of a buffer or array — hence the name overflow— and corrupt adjacent memory. When you specify a field width, you need to provide a.
Maybe modify buffer size or offset? Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate systems. Buffer overflow can lead to unexpected.